Step 5: Using a Stronger Cipher
Table of Contents
Objective: Change the default weak cipher to a stronger cipher.
6.5.1. Cautionary Notes
This method of installing OpenVPN was quick and easy. You could put these commands in a script and create a new VPN instance without effort. You could easily fool yourself into thinking that you are secure just because you can spin up a Docker-based VPN connection.
We didn’t talk about any security features. You shouldn’t rely on this Docker version or any other OpenVPN configuring until you explore the cipher and security settings of the build.
Attention
The default configuration of OpenVPN uses insecure settings.
For example, OpenVPN uses cipher BF-CBC by default, which they then acknowledge is affected by the SWEET32 attack. To mitigate this attack, they recommend using AES-256-CBC or AES-128-CBC. Furthermore, TLS version 1.0 is old and no longer trusted. OpenVPN VPN leaves it up to the end-user to choose the appropriate ciphers and security measures.
x.x.x.x:63081 peer info: IV_GUI_VER=OpenVPN_GUI_10
x.x.x.x:63081 Incoming Data Channel: Cipher 'BF-CBC' initialized with 128 bit key
x.x.x.x:63081 WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
x.x.x.x:63081 Incoming Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication
x.x.x.x:63081 WARNING: cipher with small block size in use, reducing reneg-bytes to 64MB to mitigate SWEET32 attacks.
x.x.x.x:63081 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
6.5.2. Security recommendations
OpenVPN’s community guide on Hardening OpenVPN provides recommendations. Let’s see how we can implement some of these features easily.
Recommendation |
Our Action |
|---|---|
|
Use |
|
OpenVPN uses a 2048 bits DH key by default. |
|
Enable directive |
|
Use directive |
|
We can enable TLS auth, but we have to generate new keys |
6.5.3. Changing Ciphers
Changing ciphers in OpenVPN is simple. Both sides (the client and server)
must match except tls-server for the server and tls-client for the
client.
You can use other combinations, but here is a recommendation:
Add these lines to the server config.
openvpn.conf# Uses a stronger cipher for a more secure connection cipher AES-128-CBC tls-server tls-version-min 1.2 tls-cipher TLS-DHE-RSA-WITH-AES-128-GCM-SHA256
Add these lines to the client config.
user.ovpn# Uses a stronger cipher for a more secure connection cipher AES-128-CBC tls-client tls-version-min 1.2 tls-cipher TLS-DHE-RSA-WITH-AES-128-GCM-SHA256
Restart the OpenVPN server for the changes to take effect.
Here the result after making some basic config changes. Notice that the warnings are gone.
Output without INSECURE cipher warningsx.x.x.x:50676 TLS: Initial packet from [AF_INET]x.x.x.x:50676, sid=a354af3c c087f793 x.x.x.x:50676 VERIFY OK: depth=1, CN=Easy-RSA CA x.x.x.x:50676 VERIFY OK: depth=0, CN=user2 x.x.x.x:50676 peer info: IV_VER=2.3.10 x.x.x.x:50676 peer info: IV_PLAT=win x.x.x.x:50676 peer info: IV_PROTO=2 x.x.x.x:50676 peer info: IV_GUI_VER=OpenVPN_GUI_10 x.x.x.x:50676 Outgoing Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key x.x.x.x:50676 Outgoing Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication x.x.x.x:50676 Incoming Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key x.x.x.x:50676 Incoming Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication x.x.x.x:50676 Control Channel: TLSv1.2, cipher TLSv1.2 DHE-RSA-AES128-GCM-SHA256, 2048 bit RSA x.x.x.x:50676 [user2] Peer Connection Initiated with [AF_INET]x.x.x.x:50676 user2/x.x.x.x:50676 MULTI_sva: pool returned IPv4=192.168.255.6, IPv6=(Not enabled) user2/x.x.x.x:50676 MULTI: Learn: 192.168.255.6 -> user2/x.x.x.x:50676 user2/x.x.x.x:50676 MULTI: primary virtual IP for user2/x.x.x.x:50676: 192.168.255.6 user2/x.x.x.x:50676 PUSH: Received control message: 'PUSH_REQUEST' user2/x.x.x.x:50676 SENT CONTROL [user2]: 'PUSH_REPLY,block-outside-dns,dhcp-option DNS 163.172.185.51,dhcp-option DNS 80.67.169.40,comp-lzo no,route 192.168.255.1,topology net30,ping 10,ping-restart 60,ifconfig 192.168.255.6 192.168.255.5,peer-id 0' (status=1)
6.5.4. Adding TLS Authentication
We can enable HMAC authentication using SHA256 easily, but it requires generating new client keys to use it.
Add
auth SHA256to the server config.Generate a new client.ovpn config. You will notice that it added a new section called
<tls-auth>.openvpn.confkey-direction 1 <tls-auth> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- 439bfa594cc754c616bfed3b32a1d7b7 d25bbea . . . 27922acd9a64ca76c c2aa62ae990b8e5d43f723a0785cd796 -----END OpenVPN Static key V1----- </tls-auth>
Add
auth SHA256to the client config.You will have to add the ciphers to the new client config.
Connect to the VPN server using your new key.
You can verify that it uses the more secure
SHA256HMAC authentication.
Output after enablingauth SHA256Tue Apr 23 15:22:44 2019 x.x.x.x:57670 TLS: Initial packet from [AF_INET]x.x.x.x:57670, sid=f45c37fa bf4202b6 Tue Apr 23 15:22:44 2019 x.x.x.x:57670 VERIFY OK: depth=1, CN=Easy-RSA CA Tue Apr 23 15:22:44 2019 x.x.x.x:57670 VERIFY OK: depth=0, CN=client4 Tue Apr 23 15:22:44 2019 x.x.x.x:57670 peer info: IV_VER=2.3.10 Tue Apr 23 15:22:44 2019 x.x.x.x:57670 peer info: IV_PLAT=win Tue Apr 23 15:22:44 2019 x.x.x.x:57670 peer info: IV_PROTO=2 Tue Apr 23 15:22:44 2019 x.x.x.x:57670 peer info: IV_GUI_VER=OpenVPN_GUI_10 Tue Apr 23 15:22:44 2019 x.x.x.x:57670 Outgoing Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key Tue Apr 23 15:22:44 2019 x.x.x.x:57670 Outgoing Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication Tue Apr 23 15:22:44 2019 x.x.x.x:57670 Incoming Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key Tue Apr 23 15:22:44 2019 x.x.x.x:57670 Incoming Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication Tue Apr 23 15:22:44 2019 x.x.x.x:57670 Control Channel: TLSv1.2, cipher TLSv1.2 DHE-RSA-AES128-GCM-SHA256, 2048 bit RSA Tue Apr 23 15:22:44 2019 x.x.x.x:57670 [client4] Peer Connection Initiated with [AF_INET]x.x.x.x:57670 Tue Apr 23 15:22:44 2019 client4/x.x.x.x:57670 MULTI_sva: pool returned IPv4=192.168.255.6, IPv6=(Not enabled) Tue Apr 23 15:22:44 2019 client4/x.x.x.x:57670 MULTI: Learn: 192.168.255.6 -> client4/x.x.x.x:57670 Tue Apr 23 15:22:44 2019 client4/x.x.x.x:57670 MULTI: primary virtual IP for client4/x.x.x.x:57670: 192.168.255.6 Tue Apr 23 15:22:47 2019 client4/x.x.x.x:57670 PUSH: Received control message: 'PUSH_REQUEST' Tue Apr 23 15:22:47 2019 client4/x.x.x.x:57670 SENT CONTROL [client4]: 'PUSH_REPLY,block-outside-dns,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,comp-lzo no,route 192.168.255.1,topology net30,ping 10,ping-restart 60,ifconfig 192.168.255.6 192.168.255.5,peer-id 0' (status=1)
Authentication Error
Error message TLS Error: cannot locate HMAC in incoming packet indicates that the client configs is missing directive
auth SHA256.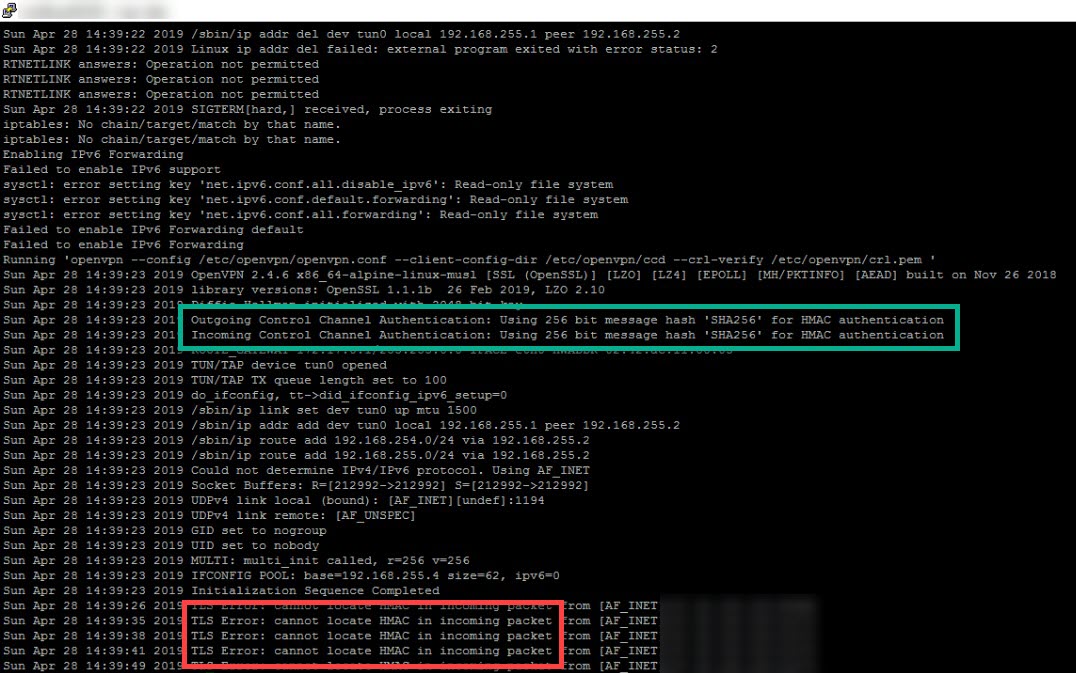
HMAC error if the client config does not include
auth SHA256