Step 4: Connect to Your VPN Server
Table of Contents
Objective: Install an OpenVPN client and connect to your server.
6.4.1. Connect to the VPN Server
Download the official OpenVPN community client if you are using Windows. Or, you can locate another OpenVPN client.
Or, download
OpenVPN-2.5.0-I601-amd64.msifrom this site directly.
Download the
user1.ovpnclient config from your VPS.Load the
user1.ovpnconfig in your OpenVPN client.Connect to the VPN server.
View the OpenVPN client log to verify that there are no errors.
6.4.2. Verify Connectivity
Note
This instructions assumes the user is using Windows
Open the Command Prompt using
cmdor find it in the application list.View the IP address and DNS settings using
ipconfigIt should be
192.168.255.6Verify the DNS settings are the same as in the
openvpn.conffile in the VPS.
Connection-specific DNS Suffix . : Description . . . . . . . . . . . : TAP-Windows Adapter V9 Physical Address. . . . . . . . . : 00-FF-94-36-EF-45 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.255.6(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.252 Lease Obtained. . . . . . . . . . : Friday, April 19, 2019 4:46:46 PM Lease Expires . . . . . . . . . . : Saturday, April 18, 2020 4:46:46 PM Default Gateway . . . . . . . . . : DHCP Server . . . . . . . . . . . : 192.168.255.5 DNS Servers . . . . . . . . . . . : 1.1.1.1 9.9.9.9 NetBIOS over Tcpip. . . . . . . . : Enabled
Ping the VPN server using the VPN gateway at
ping 192.168.255.1to verify connectivity to the VPN server.Ping a public IP address, such as 1.1.1.1 or 8.8.8.8 to verify connectivity through your VPN server.
Perform a
tracertto verify that your connection is going through the VPN connection.C:\Users\user>ping 192.168.255.1 Pinging 192.168.255.1 with 32 bytes of data: Reply from 192.168.255.1: bytes=32 time=146ms TTL=64 Reply from 192.168.255.1: bytes=32 time=146ms TTL=64 Reply from 192.168.255.1: bytes=32 time=148ms TTL=64 Reply from 192.168.255.1: bytes=32 time=146ms TTL=64 Ping statistics for 192.168.255.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 146ms, Maximum = 148ms, Average = 146ms C:\Users\user>ping 1.1.1.1 Pinging 1.1.1.1 with 32 bytes of data: Reply from 1.1.1.1: bytes=32 time=153ms TTL=54 Reply from 1.1.1.1: bytes=32 time=173ms TTL=54 Reply from 1.1.1.1: bytes=32 time=152ms TTL=54 Reply from 1.1.1.1: bytes=32 time=152ms TTL=54 Ping statistics for 1.1.1.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 152ms, Maximum = 173ms, Average = 157ms C:\Users\user>tracert -d 8.8.8.8 Tracing route to 8.8.8.8 over a maximum of 30 hops 1 151 ms 148 ms 160 ms 192.168.255.1 2 146 ms 150 ms 149 ms 172.17.0.1 3 145 ms 146 ms 146 ms 46.105.x.x 4 146 ms 148 ms 146 ms 192.168.143.254 5 149 ms 172 ms 233 ms 51.255.185.126 6 147 ms 146 ms 153 ms 10.99.169.215 7 146 ms 147 ms 171 ms 37.187.232.52 8 148 ms 151 ms 150 ms 10.95.48.10 9 154 ms 153 ms 153 ms 91.121.215.219 10 * * * Request timed out. 11 151 ms 153 ms 151 ms 108.170.244.193 12 152 ms * 150 ms 209.85.254.147 13 151 ms 151 ms 152 ms 8.8.8.8 Trace complete.
Navigate to whoer.net
Verify that the IP address is the same as your VPS
Take note that the location and ISP data.
View the anonymity score and see what affects it.
You can have a score of 90% if your DNS servers are in the same country as your IP address.
Select an IP from this list of public DNS servers to match the country where your VPS is.
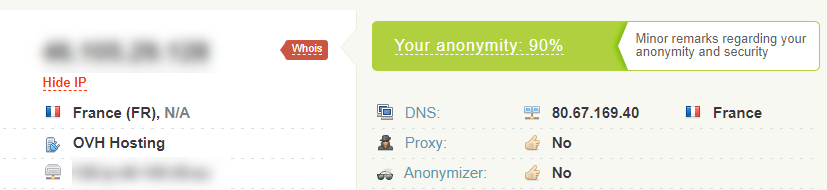
Perform an IP leak test to determine if your VPN connection is leaking your real IP or DNS information.
6.4.3. Connection Log (Server)
View the OpenVPN server log to look for warnings or errors.
docker logs openvpn
Here is a successful connection log, but notice the warnings.
x.x.x.x:63081 TLS: Initial packet from [AF_INET]x.x.x.x:63081, sid=96293170 9a0a4cd5
x.x.x.x:63081 VERIFY OK: depth=1, CN=Easy-RSA CA
x.x.x.x:63081 VERIFY OK: depth=0, CN=user1
x.x.x.x:63081 peer info: IV_VER=2.3.10
x.x.x.x:63081 peer info: IV_PLAT=win
x.x.x.x:63081 peer info: IV_PROTO=2
x.x.x.x:63081 peer info: IV_GUI_VER=OpenVPN_GUI_10
x.x.x.x:63081 Outgoing Data Channel: Cipher 'BF-CBC' initialized with 128 bit key
x.x.x.x:63081 WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
x.x.x.x:63081 Outgoing Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication
x.x.x.x:63081 Incoming Data Channel: Cipher 'BF-CBC' initialized with 128 bit key
x.x.x.x:63081 WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
x.x.x.x:63081 Incoming Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication
x.x.x.x:63081 WARNING: cipher with small block size in use, reducing reneg-bytes to 64MB to mitigate SWEET32 attacks.
x.x.x.x:63081 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
x.x.x.x:63081 [user1] Peer Connection Initiated with [AF_INET]x.x.x.x:63081
user1/x.x.x.x:63081 MULTI_sva: pool returned IPv4=192.168.255.6, IPv6=(Not enabled)
user1/x.x.x.x:63081 MULTI: Learn: 192.168.255.6 -> user1/x.x.x.x:63081
user1/x.x.x.x:63081 MULTI: primary virtual IP for user1/x.x.x.x:63081: 192.168.255.6
user1/x.x.x.x:63081 PUSH: Received control message: 'PUSH_REQUEST'
user1/x.x.x.x:63081 SENT CONTROL [user1]: 'PUSH_REPLY,block-outside-dns,dhcp-option DNS 163.172.185.51,dhcp-option DNS 80.67.169.40,comp-lzo no,route 192.168.255.1,topology net30,ping 10,ping-restart 60,ifconfig 192.168.255.6 192.168.255.5,peer-id 0' (status=1)
6.4.4. Debugging
Tip
Look at both the client log and the server log if you have connection issues.
For example, the following error displayed in the connection window is
caused by an invalid comp-lzo configuration. To correct it, ensure that
the settings are identical in both configs.
write to TUN/TAP : The data area passed to a system call is too small. (code=122)
docker logs openvpn
TLS: Initial packet from [AF_INET]x.x.x.x:64668, sid=1a9c07a1 92212f25
VERIFY OK: depth=1, CN=Easy-RSA CA
VERIFY OK: depth=0, CN=user1
peer info: IV_VER=2.3.10
peer info: IV_PLAT=win
peer info: IV_PROTO=2
peer info: IV_GUI_VER=OpenVPN_GUI_10
WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1541'
WARNING: 'comp-lzo' is present in local config but missing in remote config, local='comp-lzo'
Outgoing Data Channel: Cipher 'BF-CBC' initialized with 128 bit key
WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Outgoing Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication
Incoming Data Channel: Cipher 'BF-CBC' initialized with 128 bit key
WARNING: INSECURE cipher with block size less than 128 bit (64 bit). This allows attacks like SWEET32. Mitigate by using a --cipher with a larger block size (e.g. AES-256-CBC).
Incoming Data Channel: Using 160 bit message hash 'SHA1' for HMAC authentication
WARNING: cipher with small block size in use, reducing reneg-bytes to 64MB to mitigate SWEET32 attacks.
Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
[user1] Peer Connection Initiated with [AF_INET]x.x.x.x:64668
user1/x.x.x.x:64668 MULTI_sva: pool returned IPv4=192.168.255.6, IPv6=(Not enabled)
user1/x.x.x.x:64668 MULTI: Learn: 192.168.255.6 -> user1/x.x.x.x:64668
user1/x.x.x.x:64668 MULTI: primary virtual IP for user1/x.x.x.x:64668: 192.168.255.6
user1/x.x.x.x:64668 PUSH: Received control message: 'PUSH_REQUEST'
user1/x.x.x.x:64668 SENT CONTROL [user1]: 'PUSH_REPLY,block-outside-dns,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,comp-lzo no,route 192.168.255.1,topology net30,ping 10,ping-restart 60,ifconfig 192.168.255.6 192.168.255.5,peer-id 0' (status=1)
user1/x.x.x.x:64668 Bad LZO decompression header byte: 69
user1/x.x.x.x:64668 Bad LZO decompression header byte: 69